
Town of Salem Hacked: Comprised Data of Around 7.6 Million Users
- Salman Ahmed
- January 4th, 2019

Yesterday BlankMediaGames (BMG) has sent emails to its users regarding data breach affecting around 7.6 million users of a browser-based game “Town of Salem.”
Moreover, This data incident was first exposed on 28th of December by the official team of gaming organization to security organization “DeHashed.” The email contains the details clues of those servers that are compromised. Through these compromised servers, hackers get the access of players’ entire database.
According to DeHashed, report 7,633,234 email addresses compromise out of 8,388,894 in total. The data access by hackers includes usernames, IP addresses, emails, payment information, and passwords.
On 2nd of January, “Town of Salem” official representative posted on their forum after data breach incident:
“We do not handle money. At all. The third party payment processors are the ones that handle all of that. We never see your credit card, payment information, anything like that. We don’t have access to that information.”
Moreover, he also posted about what kind of users data accessed by hackers:
“The only important data compromised would be your Username/hashed password, IP and email. Everything else is game related data.”
The BMG official also advised users to change their “Town of Salem” passwords as a precautionary measure. The official email sent by BMG regarding data breach looks like:
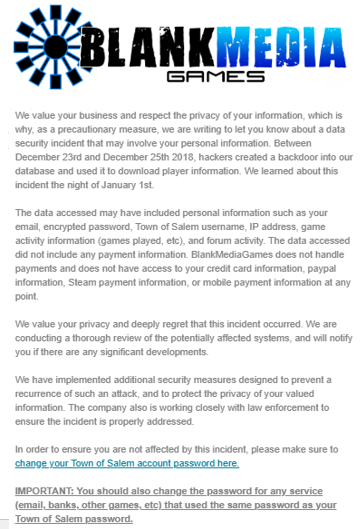
Additionally, a part of an official email sent to players, BMG also advised users, although all the passwords are safe in encrypted form, it doesn’t mean weaker passwords are safe at all. Hackers are very clever nowadays, and they can use different tools and table to decipher simple passwords.
Therefore, while updating your passwords, we recommend you to create strong passwords. Otherwise, it could cause further data breach on the different online platform due to the same email address.
Not to mention, according to one Reddit user claims that the breach more than two million passwords from the compromised database have already been decrypted and are available online:
Furthermore, this Reddit poster also provides information regarding availability of passwords on dark web.
“Initially this appeared to be restricted to some 0Day forums on the dark web. Now it is possible to find these decrypted, plaintext, passwords. By using an appropriate Google search (which I am not going to reveal here.)”
lleti says that these publicly searchable passwords do not have any additional information such as linked accounts, so the actual value of them for malicious purposes is negligible.
BMG stated that cyber thieves created the backdoor in their game to collect users data by exploiting a bug. In this way, they get illegal access to players confidential information. However, Humble Bundle clarified that no sensitive information such as customer name, billing address, password, and payment information was exposed in the incident.